NASA is preparing to outfit asteroids with robot powered guidance systems in an effort to save the Earth from an Armageddon style killer space rock.
The project, Reconstituting Asteroids into Mechanical Automata (RAMA), aims to use a series of simple robotic processes to turn space rocks into basic flying spacecraft that can be used as a planetary defense system.
Once complete, these roboticized space rocks can be
to prevent them from slamming into the Earth, James Dunn, co-founder of Made in Space, a space-manufacturing company told the Daily Mail.
After colliding with the killer asteroid, the robotized space rocks would be parked in a safe location or set on a course to fly safely out of the solar system.
ATM skimming is up 546
ATM skimming is up 546%
if you ever use an ATM, as many Americans do on a regular basis, you’re at risk for having your debit card information stolen.
If you still have the “it’ll never happen to me” perspective on fraud, here’s a stat that might persuade you to change your view: ATM card skimming incidents increased 546% from 2014 to 2015.
That figure comes from financial analytics company FICO and its FICO Card Alert Service software, which is designed to detect fraud resulting from things like debit and credit card skimming.
Unless you want to go to a physical bank branch, wait in line and work with a teller to make a withdrawal every time you want cash, you’re probably going to need to use an ATM occasionally. So, if you ever use an ATM, as many Americans do on a regular basis, you’re at risk for having your debit card information stolen. That, in turn, makes the money in your bank account vulnerable, which is problematic, given that you probably plan to use that money to pay bills, buy necessities, make loan payments and do anything else a person with a checking account does.
Demoralizing, isn’t it?
There’s not much you can do to guarantee you won’t ever fall victim to ATM skimming, other than not using ATMs, but there are ways you can manage the damage fraud causes and minimize your risk of becoming a victim in the first place. FICO reports that 60% of all skimming incidents occurred at non-bank ATMs — you might want to avoid using those. Some banks and ATMs are testing various technologies that allow account holders to withdraw money without using their cards, so you might want to see if that’s an option for you.
Upgrading to an EMV chip-enabled debit card — if your bank has not already provided one — can help, too, since the chips have a dynamic code (unlike traditional magnetic stripes) designed to make counterfeiting more difficult. In fact, the spike in card fraud could be the “last hurrah” before EMV adoption becomes more widespread.
“As the U.S. approaches chip adoption the criminals are taking this opportunity to perpetrate as much card present counterfeit fraud as possible before it is no longer viable for them to do so,” FICO said in a blog post last May when first reporting on an uptick.
Still, regardless of how you get your cash, it’s a good idea to regularly
monitor your bank accounts for signs of unauthorized activity and set up fraud alerts. That goes for all sorts of accounts — credit, debit, savings, etc. — because it’s important to your financial health and credit standing that your financial information is accurate. You can use your credit reports and scores as a way to monitor for unusual account activity (a sign of identity theft ), too. (You can can do so by viewing your free credit report summary every 30 days on Credit.com.)
DUBAI-BASED ISLAMIC SCHOLARS ISSUE FATWA AGAINST WIFI THEFT AFTER WARNING THAT FALSELY STEALING IT FROM YOUR NEIGHBOR WOULD NOT BE PROPER ISLAMIC CONDUCT
DUBAI-BASED ISLAMIC SCHOLARS ISSUE FATWA AGAINST WIFI THEFT AFTER WARNING THAT FALSELY STEALING IT FROM YOUR NEIGHBOR WOULD NOT BE PROPER ISLAMIC CONDUCT
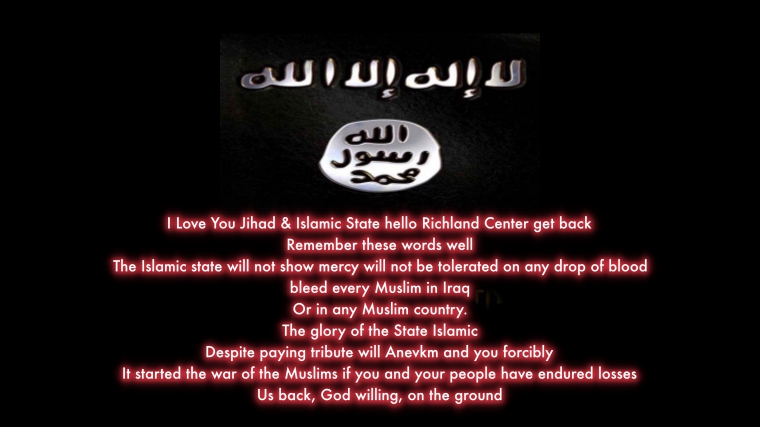
RICHLAND COUNTY WEBSITES INCLUDING SHERIFFS DEPARTMENT WERE HACKED BY PRO-ISIS HACKERS ”TEAM SYSTEM DZ” THIS FRIDAY
RICHLAND COUNTY WEBSITES INCLUDING SHERIFFS DEPARTMENT WERE HACKED BY PRO-ISIS HACKERS ”TEAM SYSTEM DZ” THIS FRIDAY
New Malware Goznym is Stealing Millions From U.S. Bank Account Holders
NEW MALWARE GOZNYM IS STEALING MILLIONS FROM U.S. BANK ACCOUNT HOLDERS
Hiding your money under your mattress may seem like an antiquated idea, but it may be the only way to stop a new hybrid malware monster that is attacking American and Canadian bank accounts. Known as GozNym, the malicious code actually combines two already powerful viruses known as Nymaim and Gozi. The resulting Trojan is as ruthless as it is resilient, and it has already been used to steal $4 million from over 24 U.S. and Canadian banks.
According to the IBM X-Force Research team that first uncovered this dangerous new weapon, which is being wielded by Eastern European hackers, GozNym takes the worst of each of its “parents.” “From the Nymaim malware, it leverages the dropper’s stealth and persistence; the Gozi ISFB parts add the banking Trojan’s capabilities to facilitate fraud via infected Internet browsers,” the IBM team writes. “The end result is a new banking Trojan in the wild.”
GozNym was first unleashed in early April, and has already inflicted considerable damage. It is unclear as of yet as to how many customers thus far have been affected, but the worst doesn’t appear to be over quite yet. IBM says that “GozNym’s operators’ top target is business accounts.” 50 percent of the attacks have been banking and credit unions, and another 17 percent of victims are retail banks.
Chinese hacker claims he can hack car without net connection!
This Chinese hacker claims he can hack Volkswagen Toureg, Audi A6, Audi A7 and more, even without an internet connection
Everyone knows that an internet-connected smart car is a huge hacking risk. Over the years it has been found that Internet connection is a must for hacking cars but a Chinese hacker thinks otherwise.
A Chinese hacker going by the handle of Daishen which means ‘stupid god’ has claimed that he can hack cars even if they are not connected to the Internet. He told Chinese tech news site Leiphone that he can hack not-so-smart cars including the Volkswagen Toureg, Audi A6, Audi A7, and likely quite a few more.
Daishen says that he can access the car’s GPS and stereo systems exploiting the flaws in car’s security layers. Daishen gave example of a particular unnamed car model, in which , the vehicle’s system runs an authentication check to prevent unauthorized system access, but stores the result of that check in plaintext rather than encrypting it, allowing a hacker to change the result from false to true and gain system access. He also said that most of the above cars had a poorly-guarded and easy to hack admin password which was meant for use by engineers and mechanics during the construction of the car. However, most of the times, the car manufacturers just forget about these default admin credentials making it easy for hackers to exploit them.
Daishen says his method of hacking cannot be carried out remotely and a hacker would need physical access to your car to get inside at least once. And once they’ve gotten access, further communication with the system could be realized in any number of ways – like a Bluetooth connection for example.
He also notes that while this kind of hack also doesn’t give the hacker total control of the car, but in the wrong hands, it can be used to track the car owner’s every move in real time via the car’s GPS navigation and use that data to rob or blackmail you. The hacker can also scare the living daylights out of you on a highway by making the stereo system play loud or shocking noises at random intervals resulting in fatal accidents.
The good news is that Daishen is a white-hat hacker and he does security research for public good. He says he’s already turned information on the security holes over to vehicle manufacturers. However, it is a fact that dumb cars are not patched often and that does leave a lot of cars vulnerable to hackers.
NASDAQ Stock Market XSs vulnerable!
Bob Greifeld , CEO of The NASDAQ Stock Market explains in a
promotional video “t hat NASDAQ is a technology based company, those businesses that we’re in have a unifying theme that are built upon our technology .”
Top technology companies such as
Google , Tesla, Amazon, and GoPro to name a few use NASDAQ as their trading exchange.
When NASDAQ “goes to a developing market and provide to them our technology, its not just the software code, its all the best practices that have been developed on a global basis that they to integrate into their operations. ”
With this information in mind, it doesn’t explain why a security researcher named analfabestia was able to discover and report a new XSS (Cross-Site Scripting) vulnerability on NASDAQ.com on January 14, 2015, The sixth such vulnerability in nearly seven years.
The vulnerability reported to
XSSposed (XSS exposed) is still unpatched putting NASDAQ users, visitors and administrators at risk of being compromised by malicious hackers. Theft of cookies, personal data, authentication credentials and browser history are probably the less dangerous consequences of XSS attacks.
NASDAQ was previously hacked back in 2010, Bloomberg BusinessWeek covered this in July 2014.
Nasdaq (NASDAQ: NDAQ) is a leading provider of trading, exchange technology, information and public company services across six continents. Through its diverse portfolio of solutions, Nasdaq enables customers to plan, optimize and execute their business vision with confidence, using proven technologies that provide transparency and insight for navigating today’s global capital markets
Twitter Back Online after Partial Disruption, Users Take to Facebook To Discuss Microblogging site 's Outage
Twitter Back Online After Partial Disruption, Users Take To Facebook To Discuss Microblogging Site’s Outage
UPDATE: 1:01 a.m. EDT — Twitter is back after a brief outage. The microblogging website went down about 10:40 p.m. EDT Wednesday and returned to normalcy post-midnight.
UPDATE: 12:17 a.m. EDT — Twitter outage is likely intermittent as users in the U.S. and Australia have complained of the service going up for a while and then becoming inaccessible after refreshing.
Some Twitter users are also complaining that the microblogging website is partially up with the notifications section not opening. Twitter said the outage is a “partial service disruption.”
“Some users may be experiencing problems reaching twitter.com and using the twitter mobile apps. We're working on a fix,” Twitter said. Meanwhile, people have taken to Facebook to discuss about the Twitter outage.
Original story:
Twitter is currently inaccessible across the United States, Japan and Australia. However, third party services, including Tweetdeck, are still working with limited functionality, according to Business Insider.
An error message shows up when users go to the Twitter website, while the mobile app hangs after refreshing the feed. The issue seems to have started 10:50 p.m. EDT Thursday.
However, Periscope and Vine services are working fine.
In January, users in Europe, U.S. and Japan complained that Twitter was down with a message: “Something went technically wrong. Thanks for noticing — we're going to fix it up and have things back to normal soon.”
The personal information of more than 50 million Filipinos has been exposed in a breach if the Philippine electoral commission!
The personal information of more than 50 million Filipinos has been exposed in a breach of the Philippine electoral commission.
According to security researchers at Trend Micro , the hack contains a huge amount of very sensitive personal data, including the fingerprints of 15.8 million individuals and passport numbers and expiry dates of 1.3 million overseas voters.
The website of the Commission on Elections, Comelec, was initially hacked on March 27 , by a group identifying itself as Anonymous Philippines, the local fork of the wider hacker collective. The homepage was defaced with a message accusing Comelec of not doing enough to ensure the security of voting machines used in the country’s upcoming election.
“One of the processes by which people exercise their sovereignty is through voting in an election,” the message read. “But what happens when the electoral process is so mired with questions and controversies? Can the government still guarantee that the sovereignty of the people is upheld?”
The same day, a different but related group, LulzSec Pilipinas, posted an online link to what it claimed was the entire database of Comelec. The 338GB database contains 75.3m individual entries on the electoral register, with 54.28m of them not tagged as disapproved – about the same number as the 54.36 million registered voters in the Philippines.
That makes this hack potentially the “biggest government related data breach in history”, according to Trend Micro, “surpassing the Office of Personnel Management (OPM) hack last 2015 that leaked PII, including fingerprints and social security numbers (SSN) of 20 million US citizens.”
It even exceeds last week’s record-breaking release of personal information from the Turkish citizenship database, which contained records on 49 million people, the population of half the country.
Trend Micro warns that the Philippine hack leaves citizens open to risk from crime. “Cybercriminals can choose from a wide range of activities to use the information gathered from the data breach to perform acts of extortion. In previous cases of data breach, stolen data has been used to access bank accounts, gather further information about specific persons, used as leverage for spear phishing emails or BEC schemes, blackmail or extortion, and much more.”
In a statement given in late March, Comelec downplayed the effect of the hack. “I want to emphasise that the database in our website is accessible to the public. There is no sensitive information there. We will be using a different website for the election, especially for results reporting and that one we are protecting very well,” a spokesman said. But Trend Micro says its investigations “showed a huge number of sensitive personally identifiable information (PII)–including passport information and fingerprint data–were included in the data dump.”
Facebook F8 attacks Indian developers as Social Network Ups Advocacy For Emerging Markets!
Facebook F8 Attracts Indian Developers As Social Network Ups Advocacy For Emerging Markets!
SAN FRANCISCO — Ime Archibong, director of strategic partnerships at Facebook, has traveled to India 10 out of the past 11 months (17 hours on a plane, each way.) The engineer-turned-manager has visited the country to meet with established businesses and startups that already employ or sign onto Facebook’s services.
Although he’s traveled elsewhere (“name any country,” he jokes), Archibong has made India a top priority. India is Facebook’s second-largest market in terms of number of active users and its fastest-growing one as more people get online. Last year, Facebook CEO Mark Zuckerberg visited New Delhi to pitch his company’s Internet.org project. “Our mission is to connect everyone in the world,” Zuckerberg said. “You can’t do that without connecting the people in India.”
But, for Facebook, the goal isn’t just to get more people onto the social network: India is also its second-largest hub of developers after the U.S. The company is looking to help business leaders and entrepreneurs create businesses with its support. “Our products that we build people in-house reach 1.6 billion around the world, but [developers are] going to be building the right and relevant tools for us to be truly global,” Archibong said.
Facebook will release more products and services Tuesday, to be announced during the company’s annual developer conference called F8. At the event, more than 2,000 developers, including partners in India, will attend panel discussions and meet with Facebook employees to get ideas on how to leverage the new offerings.
Yet, the conversations have been going on for much longer than the 48 hours to be spent at the Fort Mason Center in San Francisco. Indeed, several of the updates being released were inspired by the meetings the team has had over the last year, noted Eddie O’Neil, product manager at Facebook.
Archibong and O’Neil work on the two main pillars of Facebook’s developer relations initiative. Archibong oversees outreach and engagement, while O’Neil strategizes and creates the products for this community. They work together in that Archibong’s team will send feedback reports that can inform and have informed what O’Neil’s team builds.
“As the next billion people start to get phones and go online, there [are] developers in that billion that could use the products, services and consumer experiences we have,” O’Neil said.
Data is 2015 estimates
Facebook Penetration Around The World
The community has grown from a handful of employees six years ago, Archibong noted, to dozens in seven offices around the world. In May 2014, Facebook launched FbStart, a program to provide free tools to developers. The team is “trying to understand where [developers] are technically and culturally: different regions, different countries, that have different opportunities and challenges,” Archibong said.
For instance, Facebook developed Facebook Lite, a version of the app that uses less data and is designed for 2G networks and other slow connections, last year. The app now has 100 million monthly active users, the company announced last month.
Archibong works with the developer community to learn what is the most useful for them. That could mean helping them decide whether to create a product for Messenger, the API Facebook released last year at F8, or for the larger platform, or Facebook Lite.
Facebook’s availability and transparency has long been respected by the developer community. “Facebook has been in a consistent good ecosystem with developers and has invested in a lot. They’re handing out very good infrastructure and their documentation is great,” said Avi Flombaum, dean and co-founder of the Flatiron School, a programming school.
That enthusiasm comes even as Facebook shut down Parse, its software development kit and back end services, earlier this year. The unexpected closure did leave distrust from some developers, San Francisco Chronicle reported.
But developers are bullish on remaining services such as Facebook log-in. “People have trusted the one-tap sign-in, especially on mobile. It has a convenience and trust factor,” said Yara Paoli, director of growth at
Skyscanner, who will be attending F8.
Skyscanner, a search engine for booking travel, grew its mobile audience by 70 percent over the last year in part by running ads and connecting to the open graph on Facebook, Paoli sad. Using Facebook also allows to try to expand its reach in emerging markets, including India, following the patterns of the social network.
With Facebook, these developers are able to tap into the monthly active audience of 1.59 billion. Saavn, a musical streaming service for Indian music, has leveraged Facebook to increase its sign-ups first by connecting to the open graph in 2012.
“Given Facebook’s heavy usage across the globe and, more importantly, across emerging markets like India, the services provided by Facebook naturally boost our engagement and the richness of our own app’s offerings,” Vinodh Bhat, Saavn’s president, chief strategy officer and co-founder, wrote in an email.
For Saavn, registered users spend double the amount of time in the app compared to unregistered users, the company claims. “From a business standpoint, all of this translates into higher engagement with our products, and, therefore, increased revenue,” Bhat wrote.
Even so, by relying on Facebook, these businesses are adding vulnerabilities by being susceptible to the company’s own obstacles. For instance, Bangladesh Telecom Regulatory Authority blocked Facebook, along with a few other websites, earlier this year. That led to disruption at Prothom Alo Digital, an international news site based in Bangladesh.
“Due the blockage we could not distribute/market our content and as a result we saw a big dip in the active users/pageviews and thus a major setback for our business,” Ahteram Uddin, chief operating officer of Prothom Alo Digital, wrote in an email.
Additionally, Facebook’s Free Basics — a program to make Facebook and a set of other websites free — faced scrutiny in India after being barred by a telecom. But for Prothom Alo Digital, Free Basics is still offering a “very big chunk of daily active users,” Uddin noted and said he is supportive of the program.
Archibong, who is not directly involved in dealings with the government and telecoms over Free Basics, said he heard of good support from developers despite the pushback, with even more signing on to build for the “historically unconnected.”
“Our mission is to make truly to make the world more open and connected and give people the power to share. We know we can’t do something as crazy and big and as bold as that alone,” Archibong said.
For the developers, working with Facebook and attending F8 means quickly figuring out how to integrate the latest feature. For Skyscanner, that means following its “fail forward” mentality. “We try to gather as much as we can, implement as fast as possible. We want to encourage failing, fail forward, learn from our errors,” Paoli said.
Fbi claims its iPhone Hacking Tools can't Unlock iphone 5s,6s Plus!
FBI claims its iPhone Hacking Tool can't Unlock iPhone 5S, 6S and 6S Plus
Although everyone, including Apple, was worried about the iPhone hacking tool used by the Federal Bureau of Investigation (FBI) to access data on iPhone belonged to the San Bernardino shooter, the FBI director said the hack does not work on an iPhone 5S or later.
FBI Director James Comey said Wednesday that the agency was able to avoid a prolonged legal battle with Apple by buying a tool from a private source to hack into terrorist Syed Farook’s iPhone 5C.
Apple was engaged in a legal battle with the Department of Justice (DOJ) for a month over a court order that forces the company to write new software, which could disable passcode protection on Farook's iPhone to help them access data on it.
Apple refused to comply with the order, so the FBI worked with a third-party firm, most likely the Israeli mobile forensic firm Cellebrite, and was successfully able to access data on the locked iPhone used in the San Bernardino shooting incident last year.
But speaking to the audience during a keynote address at the biennial political science conference at Kenyon College in Ohio, Comey said the FBI's new method for unlocking iPhones does not work on most iPhone models, according to CNN.
"It's a bit of a technological corner case, because the world has moved on to [iPhone] 6’s," Comey said, describing the flaw in response to a question. "This doesn't work on sixes, doesn't work on a 5S. So we have a tool that works on a narrow slice of phones. I can never be completely confident, but I'm pretty confident about that."
FBI agrees to help unlock other iPhones (Pending Cases)
Reportedly, the FBI agreed to help the Police in Arkansas in the homicide case by unlocking an iPhone and iPod belonging to two teens accused of killing a couple.
Besides this, the agency was trying to
solve another Brooklyn case , in which an iPhone 5S that runs iOS 7 was seized in the course of a drug investigation.
But now it seems that the FBI may have to find out other options to solve its pending cases that involve newer iPhones.
Although Comey didn't elaborate on why its new hack didn't work on more advanced iPhones, it is very likely due to the Secure Enclave protections that Apple implemented with the 5S' A7 chip, which is present in all later iPhones.
Law Enforcement Agencies Worried About WhatsApp end-to-end Encryption
This isn’t the only issue bothering the FBI. Now WhatsApp supports end-to-end encryption by default for its over 1 Billion global users, which is why the FBI is worried that criminals and terrorists will take advantage of this move to hide their crime- or terrorism-related communications.
According to FBI General Counsel James Baker, the decision by the Facebook-owned messaging app to end-to-end encrypt its global offerings presents them with "a significant problem" because terrorists and criminals could "get ideas."
"If the public does nothing, encryption like that will continue to roll out," Baker
told Washington on Tuesday. "It has public safety costs. Folks have to understand that, and figure out how they are going to deal with that. Do they want the public to bear those costs? Do they want the victims of terrorism to bear those costs?"
KEPLER TELESCOPE EMERGENCY: NASA’S $600 MILLION SPACECRAFT IN TROUBLE AGAIN
For the second time now, NASA’s planet-hunting Kepler telescope is in emergency mode, National Aeronautics and Space Administration (NASA) said in a statement. As reports, the spacecraft was fully operational and in good condition last April 4, but Charlie Sobeck, Kepler and K2 mission manager at NASA’s Ames Research Center, announced how it had been discovered last April 7 that the Kepler is presently in its lowest operational mode.
The telescope is consuming a significant amount of fuel as scientists are working to find creative fixes. No one knows what exactly the problem is, and efforts are especially difficult because the spacecraft is 75 million miles away. It takes 13 minutes to register a command and receive a response on Earth. As a result, the telescope now has priority access to ground-based communication on NASA’s Deep Space Network. Emergency mode will force Kepler to continue to burn quickly through its power supply, so there’s a great deal of urgency to save the $600 million spacecraft.
Privacy for me but not for thee?FbI director James comey tapes over his webcam!
PRIVACY FOR ME BUT NOT FOR THEE? FBI DIRECTOR JAMES COMEY TAPES OVER HIS WEBCAM
Thought you were paranoid when it came your privacy? Rest assured — you’re not alone. Last week, FBI Director James Comey revealed a few of his own idiosyncrasies in keeping his private life private. Although Comey’s position in the ongoing encryption debate between
Apple and law enforcement seeks to limit privacy, a few of his comments caught the attention of those on the other side of the argument. In particular, Comey revealed that he tapes over the webcam of his personal laptop. (In some cases, hackers have been known to spy on individuals by way of the embedded camera in these personal devices.)
“I saw something in the news, so I copied it. I put a piece of tape — I have obviously a laptop, personal laptop — I put a piece of tape over the camera. Because I saw somebody smarter than I am had a piece of tape over their camera,”
Comey said. It’s an interesting admission for an individual who has long maintained that “absolute privacy” can get in the way of law enforcement and protection.
While Comey’s move is obviously a smart one (as the director of the FBI, keeping his personal matters to himself seems of the utmost importance), some activists have since suggested that his concerns are somewhat hypocritical. Even as the director calls for companies like Apple to make their devices hackable (if only be Apple itself), he’s rendering his own computer as unhackable as possible.
A few critics took to Twitter to express their discontent with Comey’s revelation, with Christopher Soghoian of the ACLU’s Speech, Privacy, and Technology Project pointing out the apparent double standard in play.












