NASA is preparing to outfit asteroids with robot powered guidance systems in an effort to save the Earth from an Armageddon style killer space rock.
The project, Reconstituting Asteroids into Mechanical Automata (RAMA), aims to use a series of simple robotic processes to turn space rocks into basic flying spacecraft that can be used as a planetary defense system.
Once complete, these roboticized space rocks can be
to prevent them from slamming into the Earth, James Dunn, co-founder of Made in Space, a space-manufacturing company told the Daily Mail.
After colliding with the killer asteroid, the robotized space rocks would be parked in a safe location or set on a course to fly safely out of the solar system.
HACKING NEWS
TECHNOLOGY
SCIENCE
Recent Posts
ATM skimming is up 546
HACKING NEWS ATM skimming is up 546%
if you ever use an ATM, as many Americans do on a regular basis, you’re at risk for having your debit card information stolen.
If you still have the “it’ll never happen to me” perspective on fraud, here’s a stat that might persuade you to change your view: ATM card skimming incidents increased 546% from 2014 to 2015.
That figure comes from financial analytics company FICO and its FICO Card Alert Service software, which is designed to detect fraud resulting from things like debit and credit card skimming.
Unless you want to go to a physical bank branch, wait in line and work with a teller to make a withdrawal every time you want cash, you’re probably going to need to use an ATM occasionally. So, if you ever use an ATM, as many Americans do on a regular basis, you’re at risk for having your debit card information stolen. That, in turn, makes the money in your bank account vulnerable, which is problematic, given that you probably plan to use that money to pay bills, buy necessities, make loan payments and do anything else a person with a checking account does.
Demoralizing, isn’t it?
There’s not much you can do to guarantee you won’t ever fall victim to ATM skimming, other than not using ATMs, but there are ways you can manage the damage fraud causes and minimize your risk of becoming a victim in the first place. FICO reports that 60% of all skimming incidents occurred at non-bank ATMs — you might want to avoid using those. Some banks and ATMs are testing various technologies that allow account holders to withdraw money without using their cards, so you might want to see if that’s an option for you.
Upgrading to an EMV chip-enabled debit card — if your bank has not already provided one — can help, too, since the chips have a dynamic code (unlike traditional magnetic stripes) designed to make counterfeiting more difficult. In fact, the spike in card fraud could be the “last hurrah” before EMV adoption becomes more widespread.
“As the U.S. approaches chip adoption the criminals are taking this opportunity to perpetrate as much card present counterfeit fraud as possible before it is no longer viable for them to do so,” FICO said in a blog post last May when first reporting on an uptick.
Still, regardless of how you get your cash, it’s a good idea to regularly
monitor your bank accounts for signs of unauthorized activity and set up fraud alerts. That goes for all sorts of accounts — credit, debit, savings, etc. — because it’s important to your financial health and credit standing that your financial information is accurate. You can use your credit reports and scores as a way to monitor for unusual account activity (a sign of identity theft ), too. (You can can do so by viewing your free credit report summary every 30 days on Credit.com.)
DUBAI-BASED ISLAMIC SCHOLARS ISSUE FATWA AGAINST WIFI THEFT AFTER WARNING THAT FALSELY STEALING IT FROM YOUR NEIGHBOR WOULD NOT BE PROPER ISLAMIC CONDUCT
TECHNOLOGYDUBAI-BASED ISLAMIC SCHOLARS ISSUE FATWA AGAINST WIFI THEFT AFTER WARNING THAT FALSELY STEALING IT FROM YOUR NEIGHBOR WOULD NOT BE PROPER ISLAMIC CONDUCT
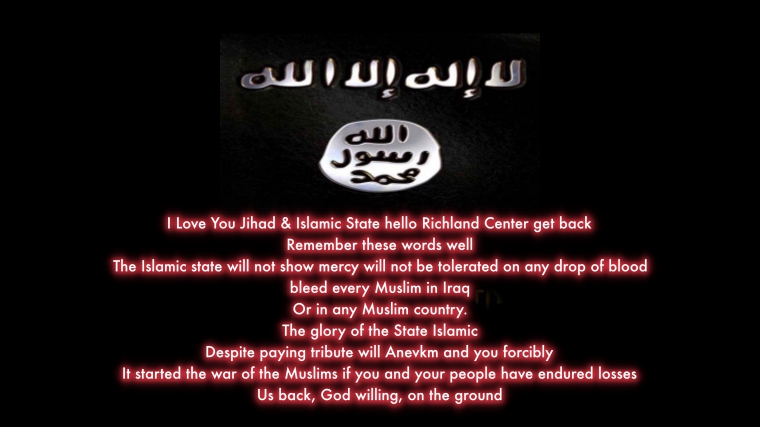
RICHLAND COUNTY WEBSITES INCLUDING SHERIFFS DEPARTMENT WERE HACKED BY PRO-ISIS HACKERS ”TEAM SYSTEM DZ” THIS FRIDAY
HACKING NEWSRICHLAND COUNTY WEBSITES INCLUDING SHERIFFS DEPARTMENT WERE HACKED BY PRO-ISIS HACKERS ”TEAM SYSTEM DZ” THIS FRIDAY
New Malware Goznym is Stealing Millions From U.S. Bank Account Holders
HACKING NEWSNEW MALWARE GOZNYM IS STEALING MILLIONS FROM U.S. BANK ACCOUNT HOLDERS
Hiding your money under your mattress may seem like an antiquated idea, but it may be the only way to stop a new hybrid malware monster that is attacking American and Canadian bank accounts. Known as GozNym, the malicious code actually combines two already powerful viruses known as Nymaim and Gozi. The resulting Trojan is as ruthless as it is resilient, and it has already been used to steal $4 million from over 24 U.S. and Canadian banks.
According to the IBM X-Force Research team that first uncovered this dangerous new weapon, which is being wielded by Eastern European hackers, GozNym takes the worst of each of its “parents.” “From the Nymaim malware, it leverages the dropper’s stealth and persistence; the Gozi ISFB parts add the banking Trojan’s capabilities to facilitate fraud via infected Internet browsers,” the IBM team writes. “The end result is a new banking Trojan in the wild.”
GozNym was first unleashed in early April, and has already inflicted considerable damage. It is unclear as of yet as to how many customers thus far have been affected, but the worst doesn’t appear to be over quite yet. IBM says that “GozNym’s operators’ top target is business accounts.” 50 percent of the attacks have been banking and credit unions, and another 17 percent of victims are retail banks.
Chinese hacker claims he can hack car without net connection!
HACKING NEWSThis Chinese hacker claims he can hack Volkswagen Toureg, Audi A6, Audi A7 and more, even without an internet connection
Everyone knows that an internet-connected smart car is a huge hacking risk. Over the years it has been found that Internet connection is a must for hacking cars but a Chinese hacker thinks otherwise.
A Chinese hacker going by the handle of Daishen which means ‘stupid god’ has claimed that he can hack cars even if they are not connected to the Internet. He told Chinese tech news site Leiphone that he can hack not-so-smart cars including the Volkswagen Toureg, Audi A6, Audi A7, and likely quite a few more.
Daishen says that he can access the car’s GPS and stereo systems exploiting the flaws in car’s security layers. Daishen gave example of a particular unnamed car model, in which , the vehicle’s system runs an authentication check to prevent unauthorized system access, but stores the result of that check in plaintext rather than encrypting it, allowing a hacker to change the result from false to true and gain system access. He also said that most of the above cars had a poorly-guarded and easy to hack admin password which was meant for use by engineers and mechanics during the construction of the car. However, most of the times, the car manufacturers just forget about these default admin credentials making it easy for hackers to exploit them.
Daishen says his method of hacking cannot be carried out remotely and a hacker would need physical access to your car to get inside at least once. And once they’ve gotten access, further communication with the system could be realized in any number of ways – like a Bluetooth connection for example.
He also notes that while this kind of hack also doesn’t give the hacker total control of the car, but in the wrong hands, it can be used to track the car owner’s every move in real time via the car’s GPS navigation and use that data to rob or blackmail you. The hacker can also scare the living daylights out of you on a highway by making the stereo system play loud or shocking noises at random intervals resulting in fatal accidents.
The good news is that Daishen is a white-hat hacker and he does security research for public good. He says he’s already turned information on the security holes over to vehicle manufacturers. However, it is a fact that dumb cars are not patched often and that does leave a lot of cars vulnerable to hackers.
NASDAQ Stock Market XSs vulnerable!
HACKING NEWSBob Greifeld , CEO of The NASDAQ Stock Market explains in a
promotional video “t hat NASDAQ is a technology based company, those businesses that we’re in have a unifying theme that are built upon our technology .”
Top technology companies such as
Google , Tesla, Amazon, and GoPro to name a few use NASDAQ as their trading exchange.
When NASDAQ “goes to a developing market and provide to them our technology, its not just the software code, its all the best practices that have been developed on a global basis that they to integrate into their operations. ”
With this information in mind, it doesn’t explain why a security researcher named analfabestia was able to discover and report a new XSS (Cross-Site Scripting) vulnerability on NASDAQ.com on January 14, 2015, The sixth such vulnerability in nearly seven years.
The vulnerability reported to
XSSposed (XSS exposed) is still unpatched putting NASDAQ users, visitors and administrators at risk of being compromised by malicious hackers. Theft of cookies, personal data, authentication credentials and browser history are probably the less dangerous consequences of XSS attacks.
NASDAQ was previously hacked back in 2010, Bloomberg BusinessWeek covered this in July 2014.
Nasdaq (NASDAQ: NDAQ) is a leading provider of trading, exchange technology, information and public company services across six continents. Through its diverse portfolio of solutions, Nasdaq enables customers to plan, optimize and execute their business vision with confidence, using proven technologies that provide transparency and insight for navigating today’s global capital markets






